Our Blog
New Security Event Analysis Tools Coming to Azure!
In today’s cybersecurity landscape, it is highly important to maintain a robust security system to cover all potential breach points in your IT environment. This can present a problem in [...]
What are Microsoft’s New Security Plans?
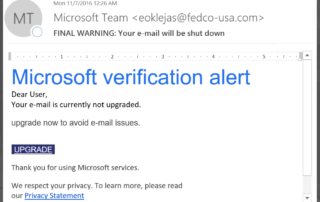
When it comes to cyber security, threats like email phishing and spoofing remain very real risks regardless of business size. To combat such threats, Microsoft has developed a number of [...]
Password-less Logins Coming to Microsoft 365
When we think about account security, we tend to consider passwords a given. As cybersecurity technologies have advanced, however, passwords have become less and less viable as a primary protection [...]
Office 365 Backup: Is it worth it?
As a cloud service, one of the major benefits of Office 365 is its reliability and resilience to various incidents that would otherwise disrupt on-premises servers. Notably, cloud hosting eliminates [...]
Is Windows Defender Good Enough? An Overview of Microsoft’s Anti-Virus
When it comes to defending against malware, installing an anti-virus is the first step many users will take. Choosing the right application can prove to be an overwhelming task, however, [...]
Phishing in 2018 – What to Look Out For
As a managed service provider, our clients often forward us emails that they suspect may be a phishing attempt. They trust us, so they often leave it to us to [...]
How to Block Ransomware in Windows 10
By John Bath We’ve written extensively about ransomware in the past, offering best practices for how users can identify threats and avoid the risks that may result in some unwarranted [...]
Expanding Security & Compliance with Data Loss Prevention
What is DLP and how can it help protect your data? We cover common features of DLP and touch on how Microsoft is taking the service a step further. For [...]
Remote Desktop vs. Virtual Private Network: Which Should You Use?
One of the major concerns of technology professionals today is to protect users and data from various cyber threats. And just as there are many things to worry about, there [...]